Evolving Cyber Threats in BFSI World
CIOReviewIndia Team | Tuesday, 27 April 2021, 14:44 IST

Just when we thought we were out of the eye of the storm, we have been swept back into it. We have been hit by the second wave of Covid-19 pandemic which is proving to be deadlier than the first one. If we look at its impact on the industry, banking sector is one of the most vulnerable ones. Many CIOs from the banking sector have confessed that they had put their cyber security initiatives on the back burner for a while after the situation improved, and they are now regretting it. In 2020, more than 2,90,000 cyber incidents were reported by the banking sector in India. This shows how susceptible the banking sector has become especially in the current times when going digital is the only way forward.
To understand how the cyber threats for the banking sector are evolving and what should be the strategy to counter them, CIOReview India organized a webinar in partnership with FireEye, one of the leading cyber security companies.
During the webinar, Anthony Ng, Vice President, Systems Engineering, APAC, FireEye shared his views on the topic. The session was divided in two parts wherein Anthony first threw light on the evolving threat landscape and then explained how the threats can be countered and mitigated.
Excerpts from the webinar:
Anthony Ng: As per our security prediction, in 2019, one of the major concerns was supply chain attacks and it continues to be one. We saw several supply chain attacks happening in 2019. In 2020, we talked about the new techniques that ransomware operators were using and how cyber-crime started becoming a value chain and it is a shared service now. Then there are geopolitical tensions which are causing a rise in the number of attacks. As the tension builds up as a result of border conflicts or policy decisions, there is an increase in espionage activities. Moreover, the increasing need to work from home has raised the concern for cloud security. Last but not the least is security validation to keep defenses and budgets in check. Whenever there is a new vulnerability, users ask the vendor if he can protect them against it and usually the vendor’s response is affirmative. But there is no way to validate his claim and if it turns out to be bogus, the cost has to be incurred by the user.
“We combined the findings of over a thousand investigations to identify the changing trends. We found that security practitioners faced a series of challenges in the past year which forced organizations into uncharted waters. APAC region experienced an overall increase in the median dwell time (duration of undetected presence of attacker in the environment). It is believed to be influenced by a greater number of intrusions with dwell times extending beyond three years. Ransomware has evolved where actors not only deploy ransomware encryptors across victim environments, but also employ a variety of other extortion tactics to coerce victims into complying with demands.
Ransomware Evolution - Traditional ransomware used to look like spam and it used to follow shotgun approach with no intrusion required and having low value return. But today the ransomwares have evolved and gained the appearance of spear phishing using sniper approach. They operate through intrusion and have high value return.
UNC2452 and Associated Clusters – FireEye has identified some threat actors and named them as UNC2452. These have low malware footprint and are almost undetectable and extremely stealthy. In this case, the attacker blends into the environment undetected. Their hostnames are according to the victim’s environment. They use a framework called In Memory Cobalt Strike BEACON. They use same IP addresses in victim’s countries to circumvent some detection rules. They use different credentials for lateral movements, which makes it difficult to identify them. They resort to temporary file replacement and task modification to remove the traces of their intrusion.
If we look at the cyber threat score of India, which is indicative of the risk involved, we see a gradual rise, especially in the financially motivated ones. The financial services cyber threat score is 9.0. Motivation of cyber criminals targeting the financial services sector are the funds and other directly valuable goods. The sector is being hit by a range of attacks like cyber-crime, cyber espionage, and hacktivism.
Mitigating the Threats
In many cases, the users say that they have done all the right things but still they are at risk. The regulators stipulate several guidelines to be followed but they cannot be too austere which can raise the cost of doing business. For the banks, the intent is to have fewer check boxes. Until it hurts you badly, you will checkbox it and move on. But the senior management is today asking whether the investment is bringing about the expected ROI and whether there is any improvement is the security posture. They are not looking for less spending, but for more sensible spending from where they can get the returns. According to Gartner, by 2025, more than 40 per cent boards of directors will have a dedicated cyber security committee overseen by a qualified board member, up from less than 10 per cent today.
Contrary to popular belief, cyber insurance is not the cure-all as it does not cover several damages such as reputational harm and future revenue loss. So, it is important to reduce or prevent business impact when prevention measure fails. One must find out what happened and what to do about it in the shortest time. One of the first things to take care of is email security as user awareness for phishing seldom works. Business email compromise and email account compromise can lead to unauthorized data access. FireEye email security solution can protect you from basic spam all the way to email impersonation. The other aspect is visibility into O365 infrastructure so that the user can see abnormal logins, brute force, e-discovery abuse and more. So, when you move to the cloud, the consideration is broader. It is not just about what I move but about what am I adopting, where are my areas of control, and so on.
Intelligence-led cyber Defense Operations – If you do not know who is coming after you, how you will defend yourself. So, threat profile becomes important. Then you can look at the footprint of the attacker to understand what they are after. This is what we call ‘hunting’. Incident detection, hunting, and incident response are the different levels of analysis. The security engineering’s key job is to make life easier for the analyst.
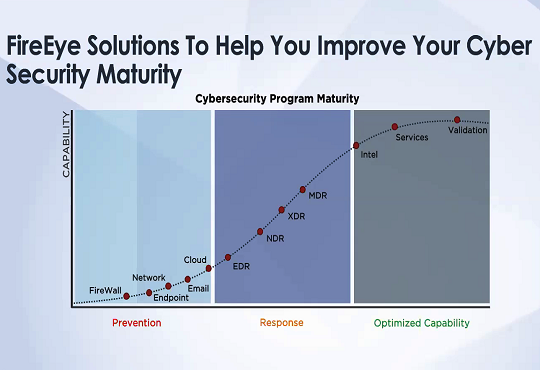
FireEye’s capability spans across the maturity curve of cyber security i.e Prevention, Response, and Optimized Capability.”
Benefitting from the valuable insights, the attendees were better informed about the approach they must follow to strengthen their cyber security posture.